5 Simple Ways to Secure Excel Sheets

Securing sensitive data within your Excel spreadsheets is more important than ever in today’s digital world. Whether you're sharing business projections, financial data, or any other confidential information, ensuring that your Excel sheets are protected is paramount. Here are five simple ways to secure your Excel spreadsheets:
1. Password Protection

Excel offers a built-in feature to password protect your spreadsheets:
- Open your Excel workbook.
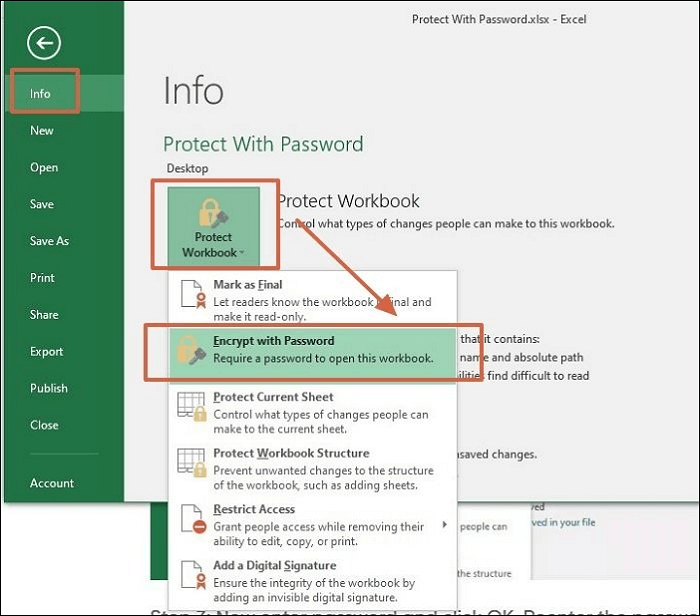
- Go to File > Info > Protect Workbook > Encrypt with Password.
- Enter a strong password. Remember, Excel uses weak encryption for older file formats, so opt for .xlsx or .xlsm.
This method will prevent unauthorized access to the workbook. However, passwords can be cracked, so use this in conjunction with other security measures.
2. Locking Cells

If you only need to secure certain parts of your spreadsheet:
- Select the cells you want to lock.
- Right-click and choose Format Cells, then go to the Protection tab.
- Check Locked to prevent editing.
- Protect the sheet by going to Review > Protect Sheet, optionally setting a password.
Only cells marked as locked will be protected once the sheet protection is enabled.
3. Limiting Access with Excel Permissions
Excel allows you to set permissions for who can open or edit the file:
- Go to File > Info > Protect Workbook > Restrict Permission by People.
- You can then choose to restrict access to individuals or groups from your organization’s directory.
This feature requires that your organization uses Windows Rights Management Services or Information Rights Management to function effectively.
4. Using Read-Only Workbooks
If you want to distribute a workbook without allowing modifications:
- Save your workbook.
- In the Save dialog, click Tools > General Options.
- Check the box for Read-only recommended.
Upon opening, users will be prompted to open as read-only, though they can choose to edit. Remember, this isn’t foolproof security but does add a layer of security by deterring accidental changes.
5. Disable Macros and VBA

Macros and Visual Basic for Applications (VBA) scripts can be used maliciously. To secure your Excel:
- Go to File > Options > Trust Center > Trust Center Settings.
- In the Macro Settings tab, disable macros or set to Disable with notification so you can decide which macros to run.
This reduces the risk of running malicious scripts but be aware that disabling macros might hinder legitimate use as well.
⚠️ Note: Even with all these measures in place, sharing files via email or cloud services can still pose risks. Always ensure that you’re sharing with the right people.
💡 Note: Remember to backup your files regularly, especially after implementing security measures, to avoid data loss.
By integrating these security practices into your routine, you'll significantly enhance the protection of your Excel spreadsheets. While no system is entirely immune to attacks, these methods provide substantial barriers to unauthorized access, reducing the risk of data breaches and ensuring that your sensitive information remains confidential.
Can I recover my password if I forget it?

+
Excel does not provide a password recovery feature. If you forget the password, you might lose access to the data unless you use specialized password recovery tools or have previously backed up an unprotected version.
Is there any way to protect the workbook entirely from editing and viewing?

+
Yes, you can encrypt the workbook with a password for both viewing and editing. However, be aware that while encryption provides security, it does not guarantee absolute protection against determined attackers.
How can I share an Excel workbook securely?

+
Share your workbook through a secure service like SharePoint, OneDrive for Business, or a similar platform with IRM capabilities. This allows you to control who can open, view, or edit the file even after sharing it.
Does password protection in Excel ensure complete security?

+
Password protection in Excel acts as a deterrent rather than a foolproof security measure. It can be bypassed with enough time and tools. Always complement this with other security strategies like encryption and restricted access permissions.